
The purpose of this post is to serve as something of a catch-all how-to for hosting multiple domains with Apache 2 on a single IP with SSL enabled for all of them. I recently underwent this process with every domain I have a website behind, and doing it correctly required information from a lot of different sources.
SNI
Hosting multiple SSL-enabled domains on a single IP address requires browsers to support something called Server Name Indication (SNI). It is supported in these browsers1:
- Internet Explorer 7 onward on Windows Vista or newer
- Mozilla Firefox 2.0 or newer
- Opera 8.0 (2005) or newer
- Opera Mobile 10.1 or newer on Android
- Google Chrome (all Vista or higher versions, Chrome 6 onward on XP, and Chrome 5.0.342.1 onward on OS X or newer)
- Safari 3.0 or newer
- Konqueror/KDE 4.7 or newer
- MobileSafari on iOS 4.0 or newer
- Android default browser on Honeycomb (v3.x) or newer
- BlackBerry 10 and BlackBerry Tablet OS default browser
- Windows Phone 7 or newer
- MicroB on Maemo
- Odyssey on MorphOS
Enabling SNI support in Apache 2.2 is very simple. Add this line to your conf file (you will probably already have a similar line for regular HTTP connections on port 80).
NameVirtualHost *:443
This is no longer necessary on Apache 2.4 as it is automatically enabled when any address/port combination appears in multiple virtual hosts2.
SSL Certificates
Any SSL certificate signed by an accepted CA will work. It does not need to be anything special like a UCC certificate (these cover multiple domains in a single certificate) or an EV certificate. The free certificates issued by a service such as StartSSL are sufficient. Each domain you want to have SSL enabled for must be named in a certificate, whether they each have one or share one.
SSL Configuration
This article covers the explanation of each of these settings much better than I ever could. Here is the TL;DR settings summary to use:
SSLCompression off
<VirtualHost *:443>
SSLEngine on
SSLCertificateFile /path/to/certificate
SSLCertificateKeyFile /path/to/private/key
# The following two lines are for StartSSL's
# intermediate certificates
SSLCertificateChainFile /etc/httpd/ssl/sub.class1.server.ca.pem
SSLCACertificateFile /etc/httpd/ssl/ca.pem
# The following line is only available on OpenSSL 1.0.2 and later
# SSLOpenSSLConfCmd DHParameters /etc/httpd/ssl/dhparam.pem
SSLOptions StrictRequire
SSLProtocol All -SSLv2 -SSLv3
SSLHonorCipherOrder On
SSLCipherSuite EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH
ServerName example.com
# Uncomment the Header line to enable HSTS
# DO NOT do this before ensuring SSL is fully working or you may lose access to the domain for six months
# Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains"
ErrorLog logs/example.com-error_log
CustomLog logs/example.com-access_log common
DocumentRoot /var/www/example.com
<Directory /var/www/example.com/>
AllowOverride All
Order Deny,Allow
Allow from All
</Directory>
</VirtualHost>
Testing
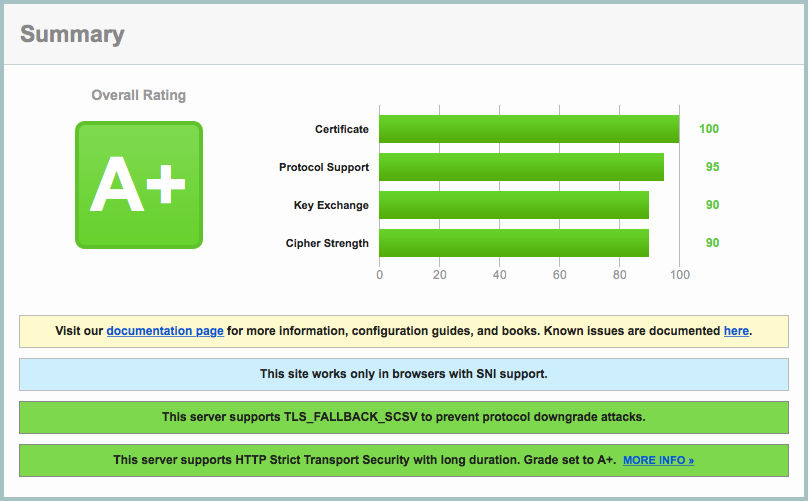
Lastly, enter your site’s address into the SSL Labs tester to verify your configuration is secure.
- This list is from Wikipedia’s Server Name Indication page ↩
- This is noted in the Apache 2.4 Upgrade Notes ↩